Do you know every person assumes the definition of terms in their own way until they are given a reference. Ever heard of the game Chinese whisper?yes the game we all played as a child in which person “A” says something to person “B”, “B” to “C” and goes till person “Z”. Almost every time, when the information moves from one person to another, it is changed. It is called the risk of interpretation.
Earlier, every organization had their own way of defining attack stages, so there was no common language which made it harder to work collaboratively, therefore, the world required something like a dictionary, that is how MITRE ATT&CK Framework was born, to make our lives easier
WHAT IS ATT&CK?
Consider ATT&CK as a social mission which has saved billions of dollars of organisations and GBs of data without even charging a penny. ATT&CK is made by a non-profit government funded organization MITRE, it is a globally-accessible knowledge base of adversary tactics and techniques.
And unlike you would think, MITRE ATT&CK framework isn’t built in a lab, or an outcome of a tabletop exercise, it is built based on the observations of real word adversaries behaviours.
It is just like an attacker playbook(contains actions that are taken based on scenarios) made by analyzing many adversaries.
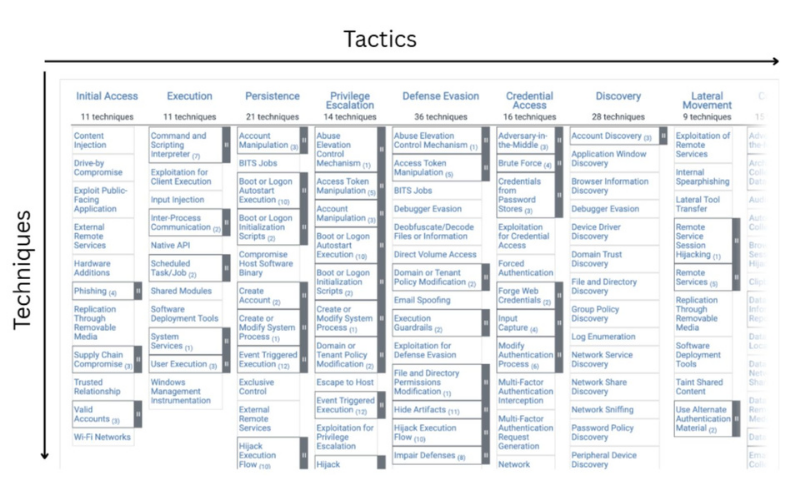
The primary purpose of developing ATT&CK was Red and Blue Teaming, as Red teaming involves simulating adversarial behaviour and ATT&CK provides detailed knowledge about adversarial behaviour. ATT&CK provided the blue team with a common language to compare notes. Understanding ATT&CK is easy, as it is made in a form of a MATRIX it is understandable with minimal research. So Lets jump on the components(WHAT, HOW, STEPS) of ATT&CK Matrix are -
We will take an example to understand the components, Imagine you want to buy a phone -
Tactics:
It means “WHAT” are the goals that attackers want to achieve, in the example your goal is to buy a phone, it means it's the tactic. Tactics includes Initial Access, Execution, Persistence, Privilege Escalation etc. Each and every tactic is very crucial, and directly helps the attacker to achieve their ulterior goal, which can be money, data etc.Techniques:
It means “HOW” the attacker will achieve a tactic, and there are multiple techniques of each tactic. In the example, Tactic is to buy a phone, but techniques are you can buy it via offline store or Online websites etc. If we take an example in technical terms, Initial Access is a tactic, but phishing which is a way via which initial access is achieved is referred to as a technique.Procedures:
These refer to the “STEPS” used by the adversaries in the past, to perform a particular technique. In the example it can be you going to a store and asking for a phone and paying for it via cash. ATT&CK shows real world examples of procedures used by the attackers like APT-28 used nmap for Active Scanning etc.These are commonly called TTPs. The combination helps security researchers to deeply understand adversarial behaviour and design their security posture. TTPs are the backbone of MITRE ATT&CK Framework.
Myths of MITRE ATT&CK Framework:
1. 100% coverage of MITRE ATT&CK is ideal for Security:
Imagine you are given a task that every day you will be sent 1000s of news articles and only 1 of them is true, you have to figure out which one, It will become too hard to handle, MITRE ATT&CK contains a vast range of techniques, if you cover all of them in your tool, the system admin actions will be flagged as an alert and your system will be full of false positives.
Therefore, this is a #MYTH BUSTED. It is recommended to prefer quality over quantity.
For techniques which aren’t covered to generate alerts, it is not recommended to lose visibility of those actions and still capture those events for threat hunting and investigation in the future.
2. MITRE ATT&CK framework is One and Done:
ATT&CK has grown since the public launch in 2015, original ATT&CK just had 50-60 techniques, now which has increased to 201+, MITRE ATT&CK has a big community which helped ATT&CK grow over the years. ATT&CK just have one rule to only add a technique if it has been performed by an adversary ever.
Therefore another #MYTH BUSTED. ATT&CK Framework is constantly evolving and updating.
3. MITRE ATT&CK is just one framework:
ATT&CK initially just had one framework, ATT&CK is constantly improving as its great team is working and improvising on consumer feedback and requirements.
ATT&CK currently have 15 different frameworks for different systems as all have different security teams which includes - Enterprise, Cloud, Windows, Linux, Industry Controlled Systems, Mobile etc.
So no one size fits all with MITRE ATT&CK Framework and we can call with #MYTH BUSTED.
4. 100% Technique coverage means 100% security:
A technique can be executed by attackers using multiple ways. So a tick in the box for each technique will only provide you with a false sense of security.Security is not a checklist game. Simply marking techniques as 'covered' ignores the nuance of how attacks are executed.
So,You need to identify and monitor the specific procedures attackers might use to implement each technique not just the technique itself.
This is also a #MYTH BUSTED.
5. ATT&CK is only for Threat Hunters and Red Teamers:
ATT&CK can be used in many ways for multiple roles like Blue teams in detection engineering, SOC Analyst in alert triage, Executives, Penetration testers and tool developers, although ATT&CK was originally built with red teaming in mind, it has since become invaluable for blue teams, SOC analysts, detection engineers, CISOs, and even security product developers which made ATT&CK important in cybersecurity for every field.
Last, #MYTH BUSTED.
SOURCES :
https://open.spotify.com/episode/6AKp1FoTnFM9VkIChdUthH?si=bb54b5a9189848f2
https://www.geeksforgeeks.org/computer-networks/what-is-mitre-att-ck-framework/
-Devesh Taneja
